Locations
DOWNLOAD
Transregional Threats Journal
Texas Series • Issue 5
Weaponizing Networks (part one): Venezuela’s Asymmetric Attack on Texas

Texas has the second largest GDP of any state in the union. It is home to some of America’s most critical warfighting capabilities and is the only state with a semi-independent electrical grid.[i] These facts alone make Texas critical to U.S. national security. These same facts make the Lone Star State a prime target for America’s adversaries – especially a less recognized, yet remarkably dangerous conglomeration of state and non-state actors in Latin America, known as the Bolivarian threat network.
Led by Cuba and Venezuela, the Bolivarian threat network unites a lengthy list of criminal groups, socialist non-governmental organizations (NGO), digital activists, media entities, political parties, terrorist organizations, and rogue regimes to wage asymmetric war against the United States. Asymmetric warfare is known conceptually as the use of non-state groups for surprise and subterfuge to achieve parity against superior opponents. The Bolivarian threat network relies on more than just non-state groups, though. It also enjoys the support of America’s near-peer adversaries in Russia and China, and from the world’s leading state sponsor of terror, the Islamic Republic of Iran.[ii]
The term “Bolivarian” is drawn from the late Hugo Chávez’s so-called Bolivarian revolution,[iii] which began as a socialist political movement that has transformed Venezuela into a criminalized state and the worst humanitarian crisis in the Western Hemisphere.[iv] Chávez exported his socialist revolutionary model to other nations in the region through a political power bloc formed in 2005 called the Bolivarian Alliance of the Americas (ALBA).[v] Although the once-powerful ALBA has lost much of its legitimacy in Latin America after the death of Chávez in 2013, it maintains an informal network of non-state actors and high-profile political figures who continue to shape political discourse in the region.
The ALBA survives through the Bolivarian threat network and Texas’ location and resources make it a chief target for this Latin American adversary. The Bolivarian threat network, as the name suggests, relies heavily on covert and overt networks that run through Texas. Whether its strategy to undermine U.S. power in the region and weaken the security of the homeland is effective hinges, in part, on its operations in the Lone Star State.
This article is the first of a three-part series where we will deconstruct how the Bolivarian threat network has penetrated Texas by utilizing Venezuelan illicit networks and legitimate oil networks to tap into the core of economic and political influence in the Lone Star State. This is part of a six-month research effort to understand how Venezuelan threat networks directly affect Texas security and prosperity. But first it is important to understand the purpose and capabilities of a modern threat network and recognize their design.
HOW THREAT NETWORKS FUNCTION
The name “criminal network” can be a misleading title. Often times the term “network” implies an arranged process to service a certain goal with terms like “intersecting” and “interconnected” to describe them.[vi] Concepts like a “chain network” come to mind, where operations resemble a supply line of people, goods, or information with end-to-end communication. Criminal networks, however, are more versatile and function like a “star or hub network,” where a central node coordinates the actions of various actors. A centralized command allows criminal organizations to maintain control of loosely connected individuals and entities within their network. The problem is these criminal networks are in a near-constant state of change and expansion.
On December 12, 2016, the U.S. Department of Defense (DoD) published Joint Publication 3-25 “Countering Threat Networks” to address the myriad of transnational and transregional threats that have converged into highly adaptive tools of asymmetric warfare. As the publication notes “threat networks use asymmetric methods and weapons and can enjoy state cooperation, sympathy, sanctuary, or supply.” These networks also increasingly blend elements of both criminal and non-criminal activity. Indeed, the modern threat networks leverage criminal and non-criminal enterprises in such a manner that law-abiding citizens can easily be caught up in an illicit network without knowing it. Admiral James G. Stavridis added that these modern, refashioned threat networks have “expanded [into] fields of diplomacy, information, military, and economic power.”[vii] The challenge then becomes making sense and then defeating ever-more-powerful networks that further blur criminal and non-criminal activity.
Figure 1: Basic Network Structure
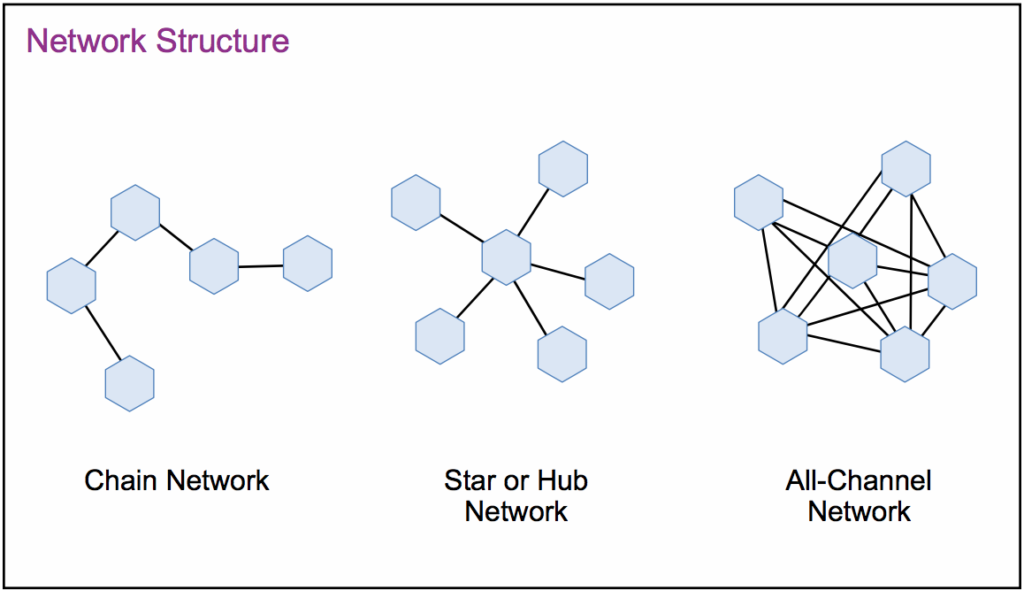
For the purposes here, the modern threat network is characterized as collaborative groups of people who may have different motivations but are formally intertwined when it benefits them against a common adversary. Some call them “all-channel networks” or “network of networks.” Regardless of the moniker, these networks have destabilized much of the modern world; and none is more relevant to Texas than the threat networks established in Venezuela.
Venezuela’s Hugo Chávez understood how threat networks enhanced asymmetric warfare capabilities and went about constructing them for those ends.[viii] Chávez designed networks in Venezuela as functional arrangements of people, goods, and products tied to illicit activities, such as drug trafficking, and to legal commercial enterprise, such as oil production and delivery. His successor, Nicolás Maduro, has advanced the reach and influence of Venezuela’s threat networks under the guise of free trade, while adhering to the Bolivarian revolution’s stated goal of undermining U.S. influence.[1] Chávez, and now Maduro, also understood that one of the most important elements for these networks, indeed any successful asymmetric warfare strategy, is the use of counterintelligence and human intelligence (CI/HUMINT) performed just below the surface.
CRIMINAL NETWORKS AS CI/HUMINT
HUMINT is an intelligence specialty where information is gathered through interpersonal contact. It is neither a practice entirely of intangibles and instinct, nor is it an exact science that can be measured and observed. Take for instance the process for creating a false identity for an undercover agent. The process demands imagination, a collection of creative minds who through experience and knowledge can sculpt the contours of that identity to fit a culture where it will exist. That process is largely artistic in nature. Backstopping the fake identity with birth certificates, college degrees, driving record, and family history requires technical abilities, which is more akin to a science. HUMINT can be an art and a science to control a person or an entire population.
In Venezuela, Hugo Chávez, with the help of Cuba’s intelligence service, known as the G2, used human intelligence to achieve countrywide control of his population. Among the most notable examples are a series of social programs created by Chávez, known as Bolivarian missions. These programs were designed to manipulate the population into government dependence, and as intended, the Venezuelan people have become reliant on the state for virtually everything. They are now mechanisms for social control.
Figure 2: Fraudulent Venezuelan Identification Card

Meanwhile, these social welfare programs were used to support the networks. One of the most consequential examples was the restructuring of Mission Identity – Venezuela’s immigration agency – where now they are responsible for creating false identities and documents for use by criminals, terrorists, and insurgents abroad.[ix] Previous reports have documented the extent to which Venezuela’s immigration system, now called SAIME, has provided identification documents to suspected members of foreign terrorist organizations, to include Hezbollah.[x] Mission Identity transformed Venezuela’s criminal and terrorist networks into a shadow intelligence service and now these networks can penetrate territories and countries where its official intelligence service, SEBIN, would struggle to, and all with plausible deniability.
This was the art behind Venezuela’s design of its HUMINT networks. Cuban and Venezuelan intelligence services were embedded in drug networks, for instance, working together in ways that Pablo Escobar could have only dreamed of. And just as the doctrine of asymmetric warfare dictates, a well-designed HUMINT network can level the playing field in the face of superior competition.[xi] These practices are now an integral part of the Bolivarian threat network.
THE ACHILLES HEEL OF U.S. NATIONAL SECURITY
The practice of counterintelligence is intended to disrupt, degrade, and preempt the HUMINT efforts of foreign intelligence services and modern threat networks. Counterintelligence is then America’s greatest defense against the Bolivarian threat networks. It is also arguably America’s greatest weakness on the state and local level, where those networks thrive.
America’s adversaries are inherently geared toward espionage and counterintelligence.[xii] After all, the central quest of an authoritarian government is the accumulation of power, resulting in a political lifestyle that survives on the manipulation and control of a given society. That manipulation comes largely through the control of information and the compromise of people – all hallmarks of the Venezuelan regimes and their allies in China, Cuba, Russia, and Iran.
The United States is at a disadvantage because our system, in a free society, is not designed with this kind of aggressive subterfuge in mind. Therefore, the United States and Texas lack the counterintelligence capabilities needed to combat the modern threat networks and their aggressive human intelligence efforts. America’s adversaries seemed to have recognized the deficiency and are directing their espionage efforts against state and local officials as a means to compromise future leaders. These authoritarian regimes have made a special effort at developing access to local officials and local markets through their networks.
California Congressman Eric Swalwell and two U.S. mayors made headlines in 2020 after being named as alleged targets of a female Chinese operative who successfully penetrated their inner circles, almost certainly to collect information and influence their decisions to the benefit of the People’s Republic of China (PRC). Intelligence services from the PRC also supposedly compromised a New York Police Department (NYPD) officer and used him to, among other things, monitor Chinese dissident communities, according to a recent federal indictment.[xiii] That officer had originally immigrated to the United States as a Tibetan refugee claiming to be escaping Chinese persecution. The indictment and timing of his arrival suggest he was sent to the United States for the express purpose of working for Chinese intelligence against dissident communities.
Another recent federal indictment accused a Massachusetts-based political scientist of being an unregistered agent of the Islamic Republic of Iran. A published author and academic, the suspect often “pitched himself to Congress, journalists, and the American public as a neutral and objective expert on Iran,” according to the indictment.[xiv] He was, however, reportedly paid by Tehran’s UN mission to spin pro-Iran narratives to the American public and in the press.
Authoritarian regimes excel at human intelligence and domestic counterintelligence because they must. They become experts in the art of identifying and neutralizing threats to their power. American society, by its nature, has less instinct for and experience with counterintelligence. Yet, officials continue to improve on those capabilities through broader cooperation and understanding of the modern threat networks.
COUNTERING THE BOLIVARIAN THREAT NETWORK
The United States is becoming more adept at countering threat networks, including those from Venezuela, through cooperation with allied nations. In February 2019, three years after the publication of JP 3-25, the U.S. Army held a “Conference of American Armies” in San Antonio, Texas, where 16 Central and South American armies, as well as some from the Caribbean, came together to address these highly adaptive threat networks. Notably left out was Venezuela and Nicaragua. Most of those countries present, regardless of political orientation, have institutionally been committed to partnering with the United States on shared challenges and threats. More importantly, they have been critical to U.S. efforts at fighting transnational and transregional threat networks, which continue to destabilize the region.
These participating countries face profound institutional and political challenges from a Bolivarian threat network intent on undermining their democracies. Under Chávez and now Maduro, the Venezuelan regime has, and remains, at the center of this effort to destabilize the entire hemisphere in order to delegitimize the United States. The regime’s candid, anti-American posture is even more evident now as it weaponizes its illicit and licit networks of drug distribution and oil shipments for the express purpose of harming American communities. It remains a potent adversary as it deploys criminal-intelligence networks to identify targets for compromise throughout Latin America, the Caribbean, and the United States.
Networks are the new “armies” of the 21st-century battlefield and combating the Bolivarian threat network itself is of crucial importance to Texas, and by extension, the United States. In parts two and three of our series, we will discuss in greater detail how the Bolivarian threat network from Venezuela is primed to challenge Texas state security and undermine broader U.S. homeland security. Evidence uncovered in SFS research suggests that Venezuela’s threat networks inside the United States were developed by commercial oil exchange and illicit narcotics distribution, targeting Texas for its proximity to the border and robust oil industry. The Maduro regime continues to nurture and leverage the Bolivarian threat network inside the United States with the intent to export the Bolivarian Revolution north.
[i] Bob Hall and David Grantham, “The Nation Depends on a Resilient Grid,” Inside Sources, January 25, 2017. Accessed: https://insidesources.com/nation-depends-resilient-grid/
[ii] For more on the “Bolivarian network” and its support from Russia, Iran, and China, see the entries in the monthly VRIC Monitor produced by the Center for a Secure Free Society, here: https://www.securefreesociety.org/research/vric-monitor-trump-to-biden-america-first-policies-aimed-at-weakening-foreign-adversaries/
[iii] Named after Simón Bolivar, a 19th-century Venezuelan leader that achieved independence for northern South America from Spanish rule. According to Chávez and Maduro, the Bolivarian revolution seeks to build a united Latin America based on 21st century socialism and free of Western influence, namely the United States.
[iv] According to USAID, Venezuela is a complex emergency. As of December 2020, there were 5.4 million Venezuelan refugees and migrants globally and another 7 million people inside Venezuela that need assistance, while the IMF reports a 25% contraction in real GDP in October 2020.
[v] The current ten members of ALBA are Antigua and Barbuda, Bolivia, Cuba, Dominica, Grenada, Nicaragua, Saint Kitts and Nevis, Saint Lucia, Saint Vincent and the Grenadines, and Venezuela. Suriname is a ‘special guest member” with previous intentions to join. Iran and Syria are observing members.
[vi] Pg. viii, Executive Summary, Commanders Overview, Joint Publication 3-25 Countering Threat Networks, Joint Chiefs of Staff, U.S. Department of Defense, December 12, 2016. Accessed: https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp3_25.pdf
[vii] James G. Stavridis, “Foreword,” Convergence: Illicit Networks and National Security in the Age of Globalization, Institute for National Strategic Studies, 2013, ix.
[viii] Max G. Manwaring, “Venezuela’s Hugo Chávez, Bolivarian Socialism, and Asymmetric Warfare,” Strategic Studies Institute, October 2005. Accessed: https://www.jstor.org/stable/resrep11239?seq=1#metadata_info_tab_contents
[ix] Joseph M. Humire, “Canada on Guard: Assessing the Immigration Security Threat of Iran, Venezuela, and Cuba,” Center for a Secure Free Society, June 4, 2014. Accessed: https://www.securefreesociety.org/research/canada-on-guard-assessing-the-immigration-security-threat-of-iran-venezuela-and-cuba/
[x] Scott Zamost, Drew Griffin, Kay Guerrero and Rafael Romo, “Venezuela may have given passports to people with ties to terrorism,” CNN, February 14, 2017. Accessed: https://www.cnn.com/2017/02/08/world/venezuela-passports-investigation/index.html
[xi] Intelligence is one of the seven critical factors in an analytical model called the “Manwaring Paradigm” developed by the Small Wars Operations Research Directorate (SWORD) of U.S. Southern Command in the 1980s. In the Manwaring Paradigm, intelligence refers to the ability to identify, locate and neutralize your adversary through timely, relevant, verified, reliable and credible intelligence.
[xii] For more on this discussion, see the interview of Joseph Humire by Sabrina Martin, “Foreign Powers Seek to destroy the Rule of Law and Social Unity in the United States,” El American, December 4, 2020. https://elamerican.com/foreign-powers-seek-to-break-the-rule-of-law-and-our-unity-joseph-humire/?lang=en
[xiii] Hollie McKay, “Chinese ‘honey trap’ could hold thousands of operatives,” Fox News, December 11, 2020: Accessed: https://nypost.com/2020/12/11/chinese-honey-trap-could-hold-thousands-of-operatives/ and “New York police officer charged with spying for China,” Yahoo News, September 22, 2020. Accessed: https://news.yahoo.com/york-police-officer-charged-spying-005433908.html?guccounter=1
[xiv] “Political Scientist Author Charged with Acting as an Unregistered Agent of The Iranian Government,” Department of Justice, January 19, 2021. Accessed: https://www.justice.gov/usao-edny/pr/political-scientist-author-charged-acting-unregistered-agent-iranian-government

